What is FHE (Fully Homomorphic Encryption)? New Premier Guide
FHE, or Fully Homomorphic Encryption, allows computations to be performed directly on encrypted data, producing results that are consistent with those obtained from the same computations on the original data. This means data can be processed and analyzed without exposing the original data, offering a new solution for protecting data privacy and integrity.
In the digital age, protecting data privacy is more crucial than ever. With the rapid development of big data, cloud computing, and IoT technology, the collection, storage, and analysis of personal information have become increasingly common. However, this also brings the risk of data breaches and misuse.
The theoretical foundation of FHE dates back to 1978, when Rivest and others proposed the first homomorphic encryption problem. It wasn’t until 2009 that Gentry constructed the first feasible FHE scheme in his doctoral dissertation, marking the true beginning of FHE research.
Early FHE schemes had extremely low computational efficiency, making them impractical for real-world applications. However, with ongoing optimizations by researchers, FHE performance has significantly improved, focusing on enhancing efficiency, reducing computational complexity, and expanding application scenarios.
Technical Implementation Paths of FHE
Ideal Lattice-Based FHE Schemes
This is currently the most practical and efficient FHE construction method. It uses the algebraic structure of ring operations, performing encryption and decryption through modular operations and decomposing ideal factors of the ring. Representative schemes include BGV, BFV, and CKKS. The advantage of these schemes is high computational efficiency, but they require larger key and ciphertext space.
Matrix-Based FHE Schemes
This approach encodes plaintext information into matrices and achieves homomorphism through matrix operations. Representative schemes include GSW and HiNC. These schemes are highly secure but less efficient.
NTRU-Based FHE Schemes
NTRU (Number Theory Research Unit) features good algebraic structure and cyclic symmetry, allowing the construction of efficient FHE schemes such as YASHE and NTRU-FHE. These schemes have the advantage of smaller key and ciphertext sizes, making them suitable for resource-constrained environments.
LWE/LWR-Based FHE Schemes
Using encryption schemes based on the LWE/LWR problem, such as FHEW and TFHE, these schemes focus more on theoretical innovation and can achieve very strong security, though practicality is limited.
FHE vs. ZKP
FHE and ZKP are both encryption technologies, but they are almost complementary.
ZKP allows a prover to prove to a verifier that a piece of information is correct without revealing specific details. The verifier can confirm the correctness and completeness of the information without re-executing the computation. While ZKP can prove correctness without leaking information, its inputs are usually in plaintext form, which may lead to privacy leaks.
FHE can solve this problem. It allows arbitrary computations on encrypted data without decryption, thereby protecting data privacy. However, FHE cannot ensure the correctness and reliability of the computations, which is precisely what ZKP addresses.
By combining FHE and ZKP, FHE protects the privacy of input data and computation processes, while ZKP provides encrypted proofs of correctness, legality, and auditability for FHE computations. This achieves truly secure and trustworthy privacy computing, which is highly valuable for sensitive data processing and multi-party collaborative computing.
ZAMA: Pioneer in FHE
Zama is an open-source cryptography company building advanced FHE solutions for blockchain and AI. It offers four main open-source solutions:
- TFHE-rs: A Rust implementation of Fully Homomorphic Encryption on Torus, used for performing Boolean and integer operations on encrypted data. The TFHE-rs library implements a Zama variant of TFHE, which includes all necessary homomorphic operations like addition and function evaluation via Programmable Bootstrapping.
- Concrete: An open-source FHE framework that includes a TFHE compiler as part of the framework, converting regular programming code into operational instructions executable by FHE, making it easy for developers to write FHE programs. Concrete’s default error probability is very low, and developers can flexibly modify this parameter.
- Concrete ML: An open-source privacy-preserving machine learning (PPML) tool built on Concrete, allowing developers to integrate FHE into machine learning models without requiring cryptographic knowledge.
- fhEVM: Integrates FHE into the EVM ecosystem, enabling developers to execute encrypted smart contracts on-chain, maintaining composability while protecting on-chain data privacy. It incorporates TFHE-rs and introduces a new TFHE Solidity library, allowing developers to compute on encrypted data using Solidity.
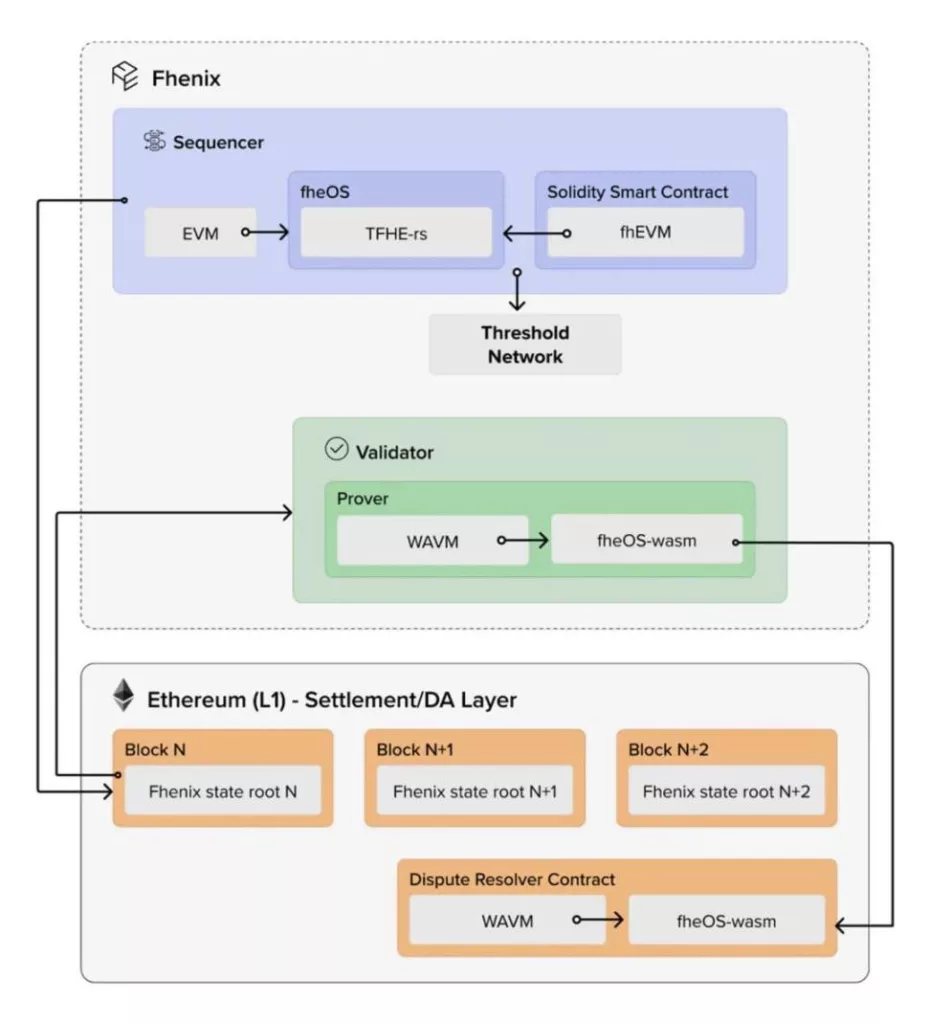
Fhenix: The First FHE-Rollup
Fhenix is the first Layer 2 rollup based on FHE, building its encrypted computation library, fheOS, on Zama’s TFHE-rs. It includes precompiled common encryption opcodes, allowing smart contracts to use FHE primitives on-chain. fheOS also handles communication and authentication between the rollup and the Threshold Service Network (TSN) for decryption and re-encryption requests, ensuring the legitimacy of decryption requests. fheOS is designed to be an extension injected into any existing EVM version, fully compatible with EVM.
Fhenix’s consensus mechanism uses Arbitrum’s Nitro prover. Fraud proofing was chosen because the underlying structures of FHE and zkSNARK differ, making it almost impossible to validate FHE computations with ZKP at the current technological stage.
Fhenix has recently partnered with EigenLayer to develop FHE coprocessors, bringing FHE computations to other public chains, L2, L3, etc. Given Fhenix’s fraud-proofing with a 7-day challenge period, EigenLayer’s service can help coprocessors achieve fast transaction confirmation, significantly improving performance.
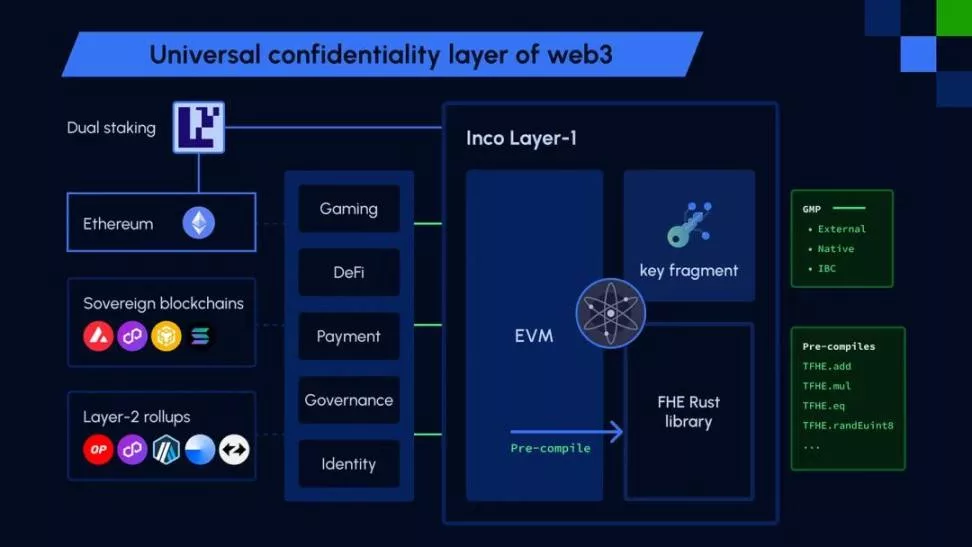
Inco Network: Confidentiality as a Service
Inco is a modular trusted computing Layer 1, serving as a universal privacy layer for Web3. It supports fhEVM, enabling developers to quickly build private Dapps using Solidity and Ethereum ecosystem development tools. Inco provides CaaS (Confidentiality as a Service) to EVM and Cosmos chains lacking native encryption through bridging and IBC protocols. CaaS services include:
- On-chain Encrypted State: Storing encrypted data directly on-chain without off-chain storage.
- Composable Encrypted State: Fully executing state transitions on encrypted data on-chain without decryption.
- On-chain Randomness: Generating random numbers on-chain for applications without external randomness services, enabling direct on-chain application development.
Inco already has several use cases, such as gaming, NFTs, RWA, voting governance, and DID.
Mind Network: FHE Restaking Layer
Mind is the first FHE restaking layer tailored for AI and POS networks. As a restaking layer, it accepts restaking tokens from ETH, BTC, and blue-chip AI companies for staking. As an FHE verification network, it uses FHE technology to verify and reach consensus on node data, ensuring data integrity and security. Mind provides economic security for decentralized AI, Depin, EigenLayer AVS, Babylon AVS, and key POS networks, maintaining system consensus and trustworthiness.
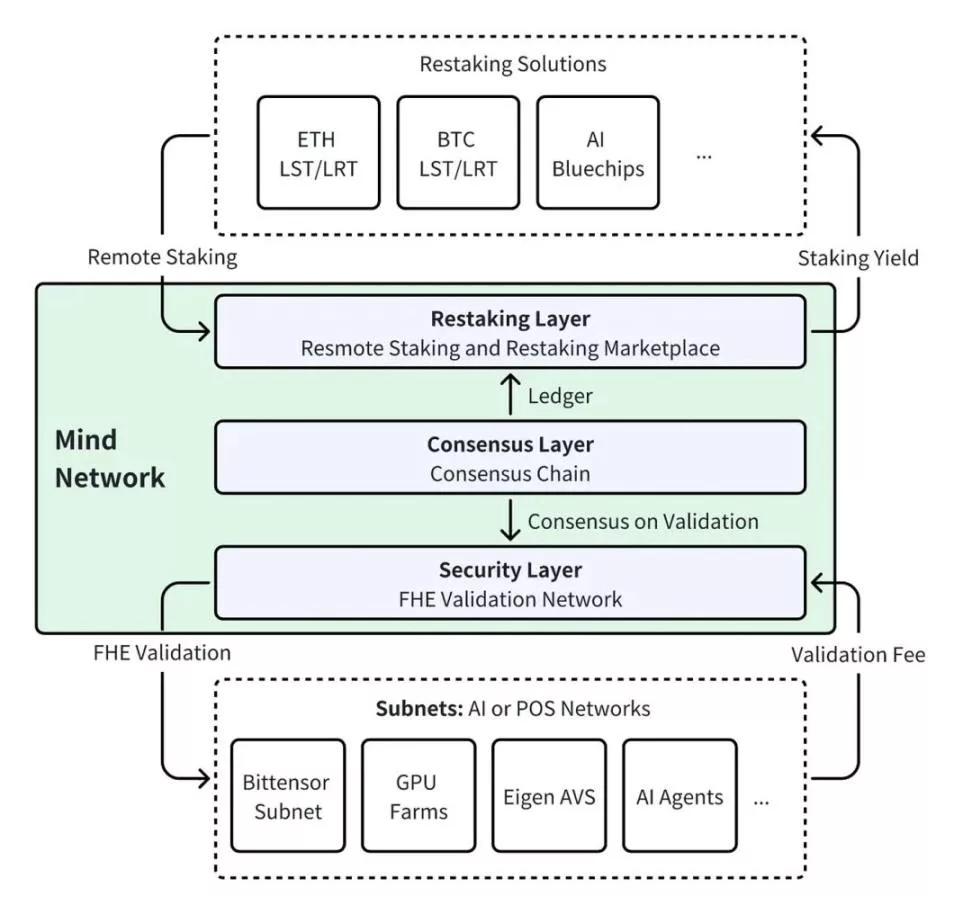
- Restaking Layer: Collaborates with EigenLayer, StakeStone, Renzo, Babylon, and Ankr for security from Ethereum and Bitcoin networks; collaborates with Chainlink CCIP and Connext for cross-chain remote restaking.
- Security Layer: Introduces FHE-enhanced verifiers to ensure end-to-end encryption of verification and consensus computation processes, integrating Fhenix and Inco’s fhEVM modules for enhanced security.
- Consensus Layer: Introduces a Proof of Intelligence (POI) consensus mechanism designed for AI tasks, ensuring fair and secure reward distribution among FHE verifiers. Mind Network is collaborating with AltLayer, EigenDA, and Arbitrum Orbit to launch rollup chains, enhancing consensus computation with lower costs and faster performance.
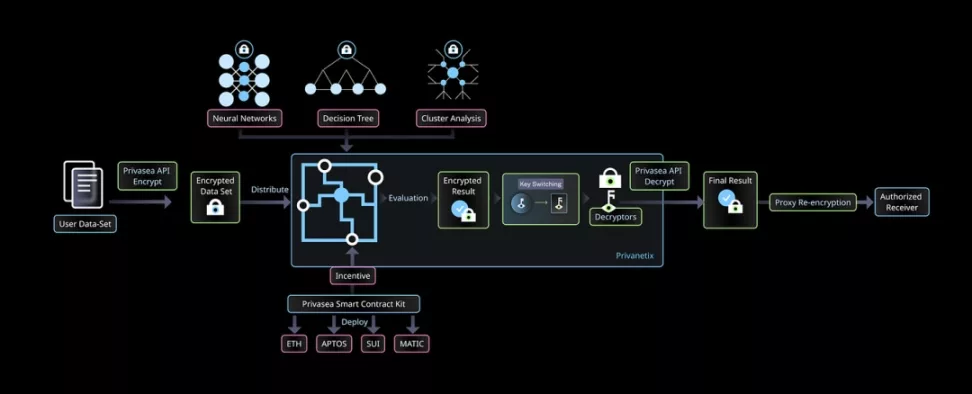
Privasea: Proof of Human
Privasea is a Depin+AI network for FHE machine learning, featuring the following core components:
- HESea Library: An advanced FHE library enabling secure computation on encrypted data, supporting various FHE schemes like TFHE, CKKS, and BGV/BFV.
- Privasea API: The application programming interface for the Privasea AI network, providing functions and endpoints to simplify data submission, model training, and predictions, ensuring encryption during transmission and processing.
- Privanetix: A decentralized computing network of high-performance nodes efficiently processing encrypted data, each node integrating the HESea library for data privacy and computational performance.
- Privasea Smart Contract Suite: A blockchain-based incentive mechanism tracking Privanetix node registration and contributions, verifying computations, and distributing rewards, ensuring participant motivation and fairness.
Privasea has launched the ImHuman application, developing Proof of Human based on FHE to verify user humanity, protecting their digital identity from robot and AI impersonation. Users can verify their humanity through facial biometrics, generating a unique NFT as proof of human identity. ImHuman allows users to securely confirm their identity on Web3 and Web2 platforms without disclosing personal details.
Conclusion
In DeFi, FHE enables transactions and fund flows without revealing sensitive financial information, protecting user privacy and reducing market risk. It may also offer a solution to the MEV problem. In blockchain gaming, FHE ensures that players’ scores and progress are protected in an encrypted state while allowing game logic to run on-chain without exposing data, enhancing fairness and security.
In AI, FHE enables analysis and model training on encrypted data, protecting data privacy and promoting cross-institutional data sharing and cooperation, driving safer and more compliant AI applications.
While FHE faces challenges in practicality and efficiency, its unique theoretical foundation offers hope for overcoming these hurdles. In the future, FHE is expected to significantly
enhance performance and expand application scenarios through algorithm optimization and hardware acceleration, providing a more robust foundation for data privacy protection and secure computing.